Local storage has seen a notable reduction in demand over the past few years. With inexpensive internet packages, users are able to explore the cloud-enabled infrastructure to stream all their files.
As the demand for cloud-based apps surged, more entrepreneurs switched to cloud models for their applications. However, there is a key concern involved with the cloud. It is cloud application security.
So, how do you secure your cloud app? Here is everything you need to know before consulting your cloud app development partner.
Table of Contents
Cloud Application Security- The Concept
Cloud computing has evolved for a long time in the past years and is not a new concept. In 1969, ARPANET (Advanced Research Projects Agency Network) built a vision to interconnect and access programmes and data at any site.
As the field saw advertisements from engineers, businesses started to build cloud-based apps. However, cloud service providers had to provide service-level agreements to win client trust with respect to their important data. Hence, cloud application security has become an important point of consideration for businesses.
Today, the popular cloud application service providers include AWS, Microsoft Azure, and Google Cloud Platform.
Read More: AWS vs Azure vs Google Cloud Platform (GCP): Which is best for your business?
Benefits of a Cloud Application Security Solution
As a result of data breaches, 51% of organizations (IBM Data Breach Report) are planning to increase their security investments. It is no doubt a fact that investing in security does offer you key benefits in the long run. Here are some of them:
- Visibility & Control: A proper implementation of cloud app security leads to better visibility and control because you have access to who is accessing what in your organization.
- 24×7 Visibility: With the detailed dashboards offered by the cloud service providers, you can keep track of your application security 24×7.
- Advanced Threat Detection: Powerful artificial intelligence models offer your application advanced threat detection services, making your organization’s and users’ data safe.
Types Of Cloud Security Compromises
Cloud security compromises can be categorized into three categories. And every category has some of the important concerns that organizations have to mitigate with cloud computing. So, here are the most popular cloud security risks, threats, and challenges.
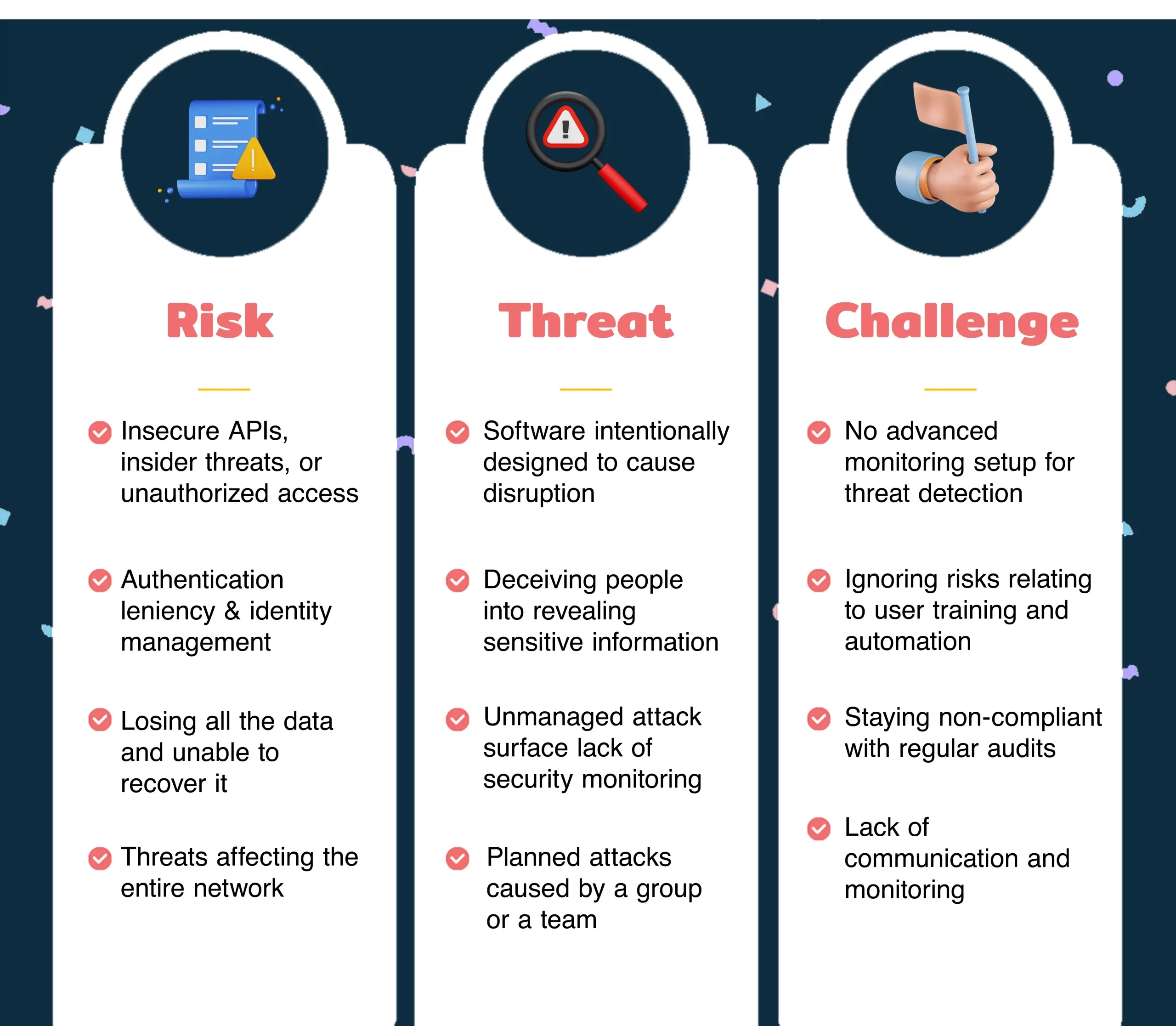
Risk
This includes potential concerns leading to the loss of data or a weak spot in security. It can be subdivided into the following:
- Data Breaches: Take place through insecure APIs, insider threats, or unauthorized access to the organizational data.
- Cloud Misconfiguration: When there is leniency in authentication and identity management or configuration, this type of risk takes place.
- Data Loss: One of the most popular security risks where organizations lose all their data and are unable to recover.
- Shared Vulnerabilities: On cloud, it is all about a network, and one threat can affect the entire network.
Threat
It is a form of attack with an offset intention. Below are some well-known threat types:
- Malware: Software intentionally designed to cause disruption to a computer or server by gaining unauthorized access.
- Phishing: Form of social engineering and scam where attackers deceive people into revealing sensitive information
- Unmanaged Attack Surface: lack of security monitoring.
- Cyberattacks: Planned attacks generally caused by a team with the same objective.
Challenge
These are hurdles to implementing practical cloud security. Here are some popular challenges:
- Visibility: No advanced monitoring setup for threat detection.
- Human Error: Ignoring risks with user training and automation for a reliable cloud environment.
- Cloud Compliance: Staying non-compliant with regular audits and necessary controls.
- Shadow IT: Lack of managing unauthorized usage through communication and monitoring for a secure IT environment.
Cloud Application Security Best Practices
The below measures collectively ensure a secure and reliable cloud environment, safeguard sensitive information, and actively address potential threats. While building your cloud computing infrastructure make sure to consider the following:

Multi-Factor Authentication
Keep your cloud apps safe by adding an extra layer of protection. Use multi-factor authentication to stop unauthorized access.
API Security Measures
Make sure your cloud is strong against threats. Use API security measures to protect your data flow and keep everything running smoothly.
Cloud Data Encryption
Lock down your important information in the cloud. Use strong encryption to make sure sensitive data stays safe and sound.
Update Cloud Apps and Servers
Don’t let your cloud get out of update. Keep things secure by regularly updating your apps and servers with the latest fixes and improvements.
Manage User Browser Sessions
Keep an eye on who’s using your cloud. Manage browser sessions well to prevent unauthorized access and keep data breaches out-of-reach.
Periodic Vulnerability Testing
Check your cloud’s health regularly. Use vulnerability testing to find and fix any weak spots before they become big problems.
Why Hire a Reliable Cloud App Development Partner for your Cloud App Security?
A reputable cloud app development company plays a pivotal role in ensuring the security of your cloud-based applications. Through their extensive experience, the team brings valuable insights and expertise to mitigate the risks, threats, and challenges of cloud security.
When you pick a reputable company, you unlock a commitment to secure and high-quality cloud applications, contributing to the success of your application and overall business.
Frequently Asked Questions
Q1. What are the cloud application security issues?
Common cloud application security issues include data breaches, unauthorized access, insecure API integration, and inadequate encryption measures.
Q2. What are the types of cloud security?
Cloud security encompasses various types, such as data security, network security, identity management, and compliance.
Q3. What is cloud application security?
Cloud application security involves implementing measures to protect cloud-hosted applications and data from cyber threats, ensuring confidentiality, integrity, and availability.
Q4. How do I secure the network of cloud-based applications?
Secure cloud-based application networks by employing encryption, implementing robust access controls, regularly updating software, and conducting thorough vulnerability testing to defend yourself against potential cloud app compromises.











 India
India USA
USA Australia
Australia Canada
Canada UK
UK UAE
UAE