In the digital world, Android is one of the widely used platforms by users and they transmit a huge amount of data using multiple platforms. To gain an idea, nearly 500 hours of content is uploaded daily only on the YouTube Platform. And, in the world of the internet where Android mobile apps are dominating the market, mobile app security becomes a key challenge for the entrepreneur. However, with the increasing risk of data leakage, there are certain ways to avoid data leakage and ensure robust mobile app security.
Table of Contents
What Exactly Is Data Leakage In Mobile App Security?
App development companies must focus on securing data leakage since it is one of the confidential parts of every Android application. But what exactly is data leakage?
Data leakage within mobile app security relates to the unauthorized access of user information from a mobile app. It happens while the user is transmitting information from one source to another source and hackers breach the data through weak leakage points. Furthermore, the outcome of data leakage can be very challenging for organizations since it highly affects their brand image and customer trust.
What Causes Data Leakage In Android Mobile Applications?
Data leakage is common throughout the world. For example, 22 accounts are being hacked every minute in Australia and every mobile app development company in Australia must ensure mobile app security for businesses. The leak can occur due to various factors and vulnerabilities. Hence, here are some common causes of data leaks in mobile apps:
- Insecure Data Storage: If private elements like passwords, personal info, or money matters are not guarded well on a device, they could get into the wrong hands.
- Weak Authentication and Authorization: Sometimes, the locks that keep the hackers out of apps do not work well. This means people who should not can get access and alter or use the important info.
- Inadequate Encryption: When apps talk to servers without using secret codes, hackers’ people can listen to the data at loopholes and disturb the information.
- Improper Permissions: Some apps ask for too many permissions that they do not really need. This can accidentally let hackers access the private data of the users.
- Vulnerable Third-Party Libraries: Apps can use third-party libraries to perform the desired activities. However, it may lead to problems like data affecting important data.
- Middleman Attacks: People who want to assist hackers can let them sneak in between an app and its servers to change useful information.
- Insecure Network Connections: If apps use weak Wi-Fi or paths without security, people nearby can see and access the private info using multiple hacking methods.
- Caching and Local Storage Issues: Sometimes, info that is stored on the device in the form of a cache is not kept secure, letting the data leak.
- Logging and Debugging Oversights: Apps sometimes write down security codes during the debugging process and if the debugging logs are not secured it can help hackers to perform data breaches.
- Lack of Regular Security Updates: If apps do not get regular checkups and fixes, the data stays at risk making it easy for hackers to break the security patterns.
- Insufficient Security Testing: Mobile app development companies must implement strong security testing and any ignorance in the process may lead to data leakage.
How To Prevent Data Leakage In Android Applications To Ensure Mobile App Security?
Preventing data leakage in Android applications involves implementing a combination of security patterns. Additionally, these patterns can be in the form of coding practices, encryption, permissions management, and regular security assessments. Here are some steps you can take to minimize the risk of data leakage:
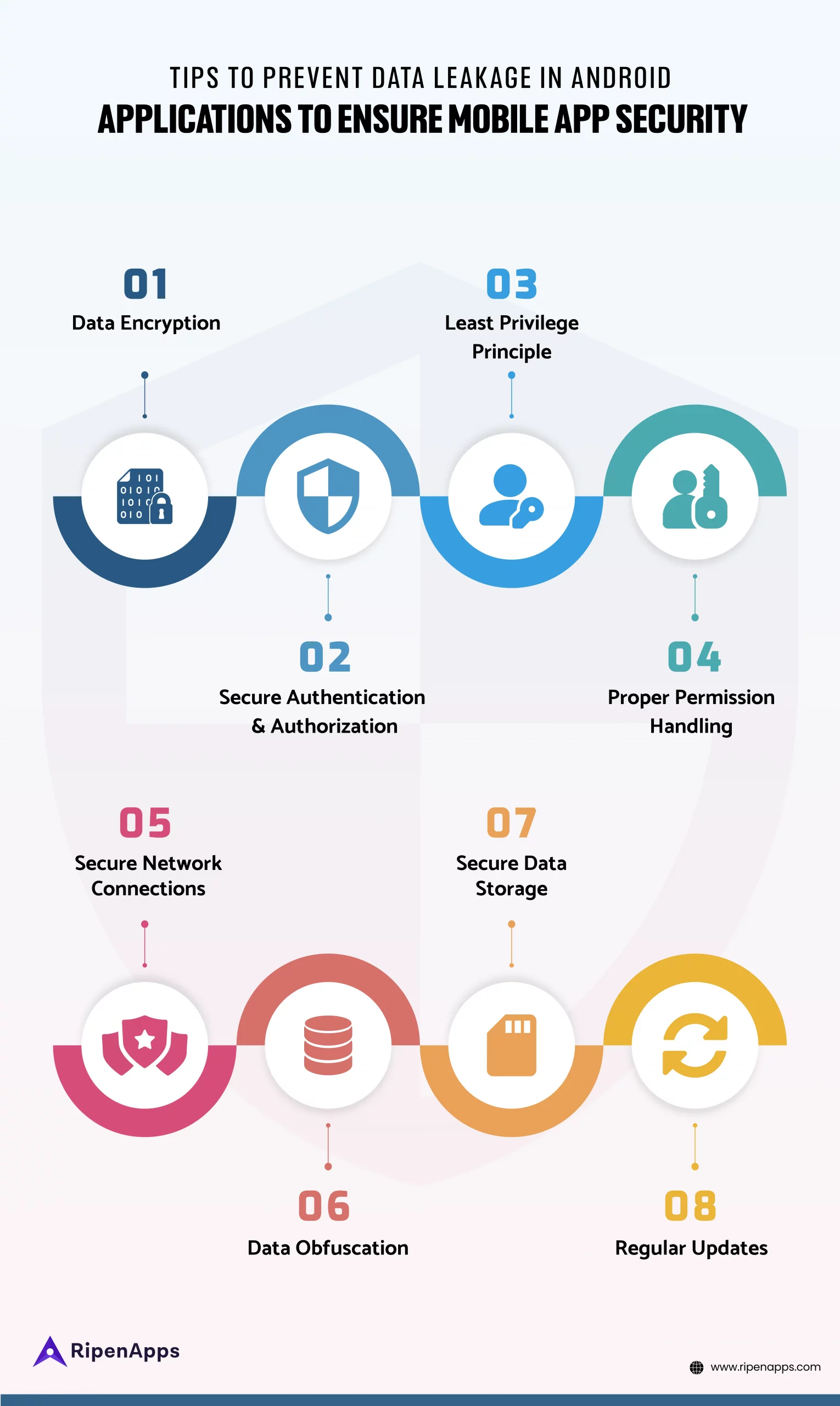
Data Encryption
Ensure that sensitive data that is stored on the device and during the transmission is properly encrypted using advanced encryption techniques. With strong data encryption, you will deliver the desired security to the users and save their data from unauthorized access.
Secure Authentication and Authorization
Multi-factor authentication and proper authorization controls are a few of the important mechanisms to secure authentication. As a result, it ensures that users only have access to the data they have permission or should use.
Least Privilege Principle
Request only the permissions necessary for your app’s functionality. Hence, minimize the number of permissions your app asks for to reduce the potential attack surface.
Proper Permission Handling
For building a safe Android mobile app follow a regular review process and audit the permissions requested by your app. Your application should only ask for the required permissions for its working and avoid the permissions that are not required. Finally, after getting the permissions to ensure that your Android app handles permission requests strategically keeping the security protocols at the top.
Secure Network Connections
Use HTTPS with valid SSL certificates for all transmission of information between your app and remote servers. Furthermore, avoid using unsecured Wi-Fi networks for sensitive transactions since they are prone to data leakage. Additionally, Android tools like Nogotofail give you an easy way to confirm that your apps are safe against known TLS/SSL vulnerabilities and misconfigurations
Data Obfuscation
The primary goal of data obfuscation is to protect sensitive data from unauthorized access and maintain data privacy while still allowing certain aspects of the data to be used for testing, analysis, or other legitimate purposes. Furthermore, Obfuscate your app’s code to make it harder for attackers to reverse-engineer and understand your app’s inner workings.
Secure Data Storage
Use Android’s secure storage options, such as the Keystore API, to store sensitive data like passwords, encryption keys, and tokens. Avoid storing sensitive data in plain text.
Regular Updates
Your Android app libraries should remain up to date and with the latest security patches. It updates your application to the latest security vulnerabilities. You can use ProviderInstaller to patch the security provider.
Third-Party Library Security
Be cautious when integrating third-party libraries and APIs. In order to ensure it, choose well-maintained and reputable libraries, and keep them updated to their latest secure versions.
Input Validation
Data leakage in Android applications is common during the input of users. Hence, it is crucial to validate user input to prevent any possible attacks during the input process.
Logging Practices
Be cautious about what data you log. Avoid logging sensitive information and sanitize any logged data to prevent accidental exposure.
Secure Coding Practices
Both Apple and Google ensure important guidelines either in application publication or during the coding process. Hence, stick to the coding guidelines, such as output encoding and input validation, to prevent the risk of data leak for sensitive data. Additionally, Take necessary measures to security your Android application to win the app development market.
Security Testing
Perform regular security assessments, such as penetration testing and code reviews, to identify and address potential vulnerabilities before they are exploited.
User Education
Educate your users about proper security practices, like not sharing sensitive information or granting excessive permissions to apps.
Privacy Policy
Clearly communicate your app’s data handling practices and privacy policies to users so they understand how their data will be used and protected. In order to ensure the privacy of users, read HIPAA COMPLIANCE in app development to gain info associated with health application development.
App Signing
Sign your app’s code with a digital signature to ensure its integrity and authenticity. This helps users trust that they are installing the legitimate version of your app.
Secure Development Lifecycle
Do not avoid security at less demanding phases of the app development lifecycle. You must incorporate security practices throughout your app’s development lifecycle right from the design process to the testing and deployment phase.
Do You Want To Avoid Data Leakage In Your Android Mobile App? Work With Top Android App Development Company
From robust data encryption, secure authentication to proper permission handling, and regular updates, RipenApps will ensure all your mobile app security needs. We are the top Android app development company in Australia, USA, and India. Our team of nearly 200 app development experts ensures that your application leaves no loopholes for data leakage. This in turn further ensures your business a solid brand value and customer trust.
FAQs
What are the types of security for mobile apps?
Mobile App security can be of multiple types however there are 4 major types. It includes authentication, authorization, encryption, logging, and extensive security testing of the application.
How do I secure my mobile apps?
In order to ensure mobile app security, you must implement a few practices.
- Ensuring safe communication between apps.
- Ask for credentials where sensitive information is visible.
- Apply network security measures for risky network connections
- Encrypt the information
- Ask for desired permissions and handle it with care
Why is mobile app security important?
Mobile app security is essential for multiple benefits. It is useful for Securing user’s
- Credentials
- Passwords
- Payment information
How does mobile app security work?
Mobile app security works by protecting data inside the application. The important data needs a separation from the application’s run time environment to prevent data leakage.










 India
India USA
USA Australia
Australia Canada
Canada UK
UK UAE
UAE